See how AI in cybersecurity is pushing boundaries beyond human capabilities, ensuring unmatched protection. As businesses and individuals increasingly rely on digital platforms for everything from commerce to communication, the potential for cyberattacks has risen dramatically. These threats are becoming more frequent and sophisticated, exploiting vulnerabilities in new and complex ways. Traditional security measures, often reliant on predefined rules and manual intervention, need help to keep pace with these dynamic threats, leading to a reactive rather than proactive approach to cybersecurity.
1. Introduction to AI in Cybersecurity
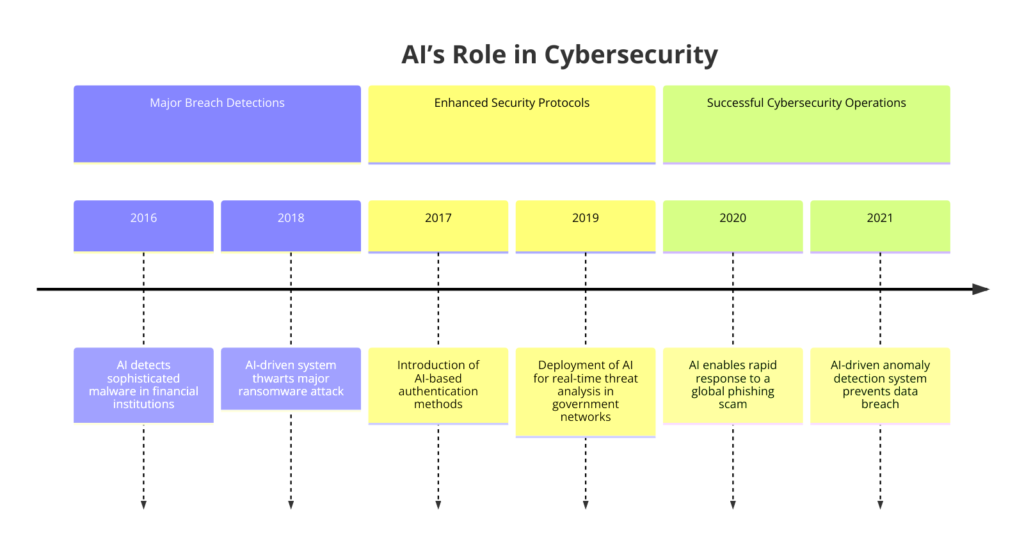
The advent of Artificial Intelligence (AI) in cybersecurity has marked a turning point in countering these threats. With its ability to process vast amounts of data at speeds and scales beyond human capability, AI offers a new paradigm in threat detection, prevention, and response.
By harnessing the power of machine learning, deep learning, and other AI methodologies, cybersecurity systems can now identify patterns, anomalies, and potential threats in real time, adapting to new information and evolving threats dynamically.
The role of AI in cybersecurity extends beyond mere automation. It encompasses developing intelligent systems capable of predictive analysis—forecasting potential security incidents before they occur and mitigating risks proactively.
This capability is revolutionary, shifting the cybersecurity approach from defensive to offensive, allowing for anticipation of cyber attackers’ moves and strengthening defenses accordingly.
AI-driven cybersecurity tools are designed to learn and evolve.
They analyze past incidents, understand cyber adversaries’ tactics, techniques, and procedures (TTPs), and continuously refine their algorithms to detect and neutralize new threats.
This ongoing learning process ensures that AI-driven cybersecurity solutions remain effective, even as cyber threats evolve.
Moreover, AI enhances cybersecurity measures by enabling more efficient resource allocation.
By automating routine tasks and decision-making processes, AI frees up human security experts to focus on more strategic, high-level tasks.
This increases the speed and efficiency of cybersecurity responses and improves the job satisfaction and effectiveness of cybersecurity personnel.
However, integrating AI into cybersecurity is challenging. Issues such as data privacy, the potential for AI-driven systems to be exploited by cyber attackers, and the ethical considerations of automated decision-making are pertinent and require careful navigation.
Despite these challenges, the potential benefits of AI in cybersecurity are undeniable.
As we delve deeper into the specifics of AI applications in threat detection, network security, and incident response in the following sections, it’s clear that AI is not just an optional tool in the cybersecurity arsenal—it’s becoming indispensable.
The future of cybersecurity lies in leveraging AI’s capabilities to create more resilient, responsive, and proactive security environments. In doing so, we can not only defend against today’s cyber threats but also anticipate and neutralize tomorrow’s threats.
2. AI in Threat Detection and Prevention
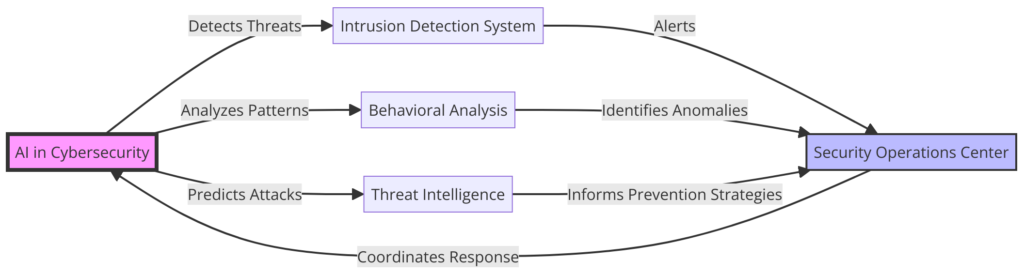
In cybersecurity, rapidly detecting and preventing threats is paramount to protecting digital assets and information.
While effective against known threats, traditional threat detection methods often need help to keep pace with the constant evolution of cyber-attack strategies.
This is where Artificial Intelligence (AI) offers a dynamic and adaptive solution to modern cybersecurity challenges.
Leveraging AI for Real-Time Threat Detection
AI algorithms, particularly those based on machine learning and deep learning, excel in identifying and understanding patterns within data.
When applied to cybersecurity, these algorithms can sift through vast quantities of network traffic, logs, and user behaviors in real-time, searching for anomalies or patterns indicative of malicious activity.
Unlike traditional systems, AI-driven solutions do not solely rely on known threat signatures.
They learn from the data they process, enabling them to detect new and emerging threats that have not been previously identified.
One of AI’s key strengths in threat detection is its ability to continuously learn and adapt.
As new data is ingested, AI models fine-tune their understanding of regular and suspicious activity within a particular network environment.
This self-improving capability ensures that AI-driven threat detection systems become more effective, staying ahead of cyber attackers who constantly change their tactics.
Examples of AI-driven threat Detection Systems
- Intrusion Detection Systems (IDS): Modern IDSs use AI to analyze network traffic in real-time, identifying unusual patterns that may signify an intrusion. By employing machine learning algorithms, these systems can differentiate between benign anomalies and genuine threats, reducing false positives and enabling security teams to respond more effectively to actual incidents.
- Endpoint Detection and Response (EDR): EDR platforms utilize AI to monitor endpoint activities, detecting and responding to malware, ransomware, and phishing attacks. AI algorithms analyze behavior logs from endpoints to identify malicious actions that deviate from established patterns, allowing for rapid containment and remediation.
- Phishing Detection: AI models are trained on vast datasets of phishing emails to identify the subtle cues that distinguish these malicious communications from legitimate messages. AI-driven systems can alert users to potential phishing attempts before they compromise sensitive information by analyzing email content, including text and metadata.
The Impact of AI on Threat Detection and Prevention

The integration of AI into threat detection and prevention strategies has profoundly impacted the cybersecurity landscape. AI-driven systems offer several key advantages:
- Speed and Efficiency: AI can analyze data at a scale and speed unattainable for human analysts, enabling real-time detection and response to threats.
- Proactive Security Posture: By identifying threats before they cause harm, AI enables organizations to shift from a reactive to a proactive security posture.
- Adaptability: AI systems adapt to new threats and changing environments, ensuring that security measures remain effective.
- Reduced False Positives: Advanced AI algorithms can more accurately distinguish between normal behavior and genuine threats, improving the efficiency of security operations.
In conclusion, AI’s role in threat detection and prevention is transformative, offering sophisticated tools to combat cyber threats in an ever-evolving digital landscape.
By harnessing the power of AI, cybersecurity professionals can enhance their defenses, reduce response times, and foster a more secure and resilient digital environment.
As we continue to face new and sophisticated cyber threats, the importance of AI in maintaining robust cybersecurity defenses will only grow, underscoring the need for ongoing innovation and adaptation in AI-driven security solutions.
3. AI in Anomaly and Fraud Detection

In the ever-evolving landscape of cyber threats, quickly and accurately identifying anomalies that may indicate fraud or a security breach is invaluable.
Artificial Intelligence (AI) plays a crucial role in this domain, offering advanced capabilities for detecting irregular patterns and activities that deviate from the norm.
Through machine learning and deep learning techniques, AI systems can sift through massive datasets, identify outliers, and flag potential threats with a level of precision and efficiency that is unattainable through manual processes.
Utilizing AI for Enhanced Anomaly Detection
AI-based anomaly detection systems operate by learning what constitutes normal behavior within a given dataset or system.
This learning process involves analyzing historical data to understand the baseline of normal activities.
Once this baseline is established, the AI system can monitor for deviations that may signify fraudulent activities, security breaches, or other malicious actions.
AI’s strength in this context lies in its ability to process and analyze data at scale, adapt to new patterns, and minimize false positives, which are common challenges in anomaly detection.
Case Studies of AI in Anomaly Detection
- Financial Fraud Detection: Financial institutions worldwide are leveraging AI to combat fraud. For instance, a leading bank implemented a machine learning-based system to monitor real-time transactions and compare them against established customer behavior patterns. The system can detect anomalies such as unusual transaction amounts, frequencies, or locations and flag them for further investigation. This proactive approach has significantly reduced fraudulent transactions, saving millions annually.
- Healthcare Fraud Detection: AI is also making strides in detecting fraud within the healthcare sector. A healthcare analytics firm developed an AI solution that analyzes billing data across millions of claims to identify patterns indicative of fraudulent activities, such as billing for services not rendered or upcoding. This AI-driven approach has uncovered substantial fraud, leading to fund recovery and improved system integrity.
- Cybersecurity Breach Detection: In cybersecurity, AI systems detect anomalies that could indicate a breach. A notable example is a cybersecurity firm that uses AI to monitor network traffic, identifying unusual data transfers or access patterns that could signify a data breach. The firm can initiate a swift response by detecting these anomalies early, mitigating potential damage.
The Impact of AI on Anomaly and Fraud Detection
The application of AI in anomaly and fraud detection has demonstrated significant benefits, including:
- Improved Detection Accuracy: AI’s ability to analyze complex data patterns enables more accurate identification of fraudulent activities and security breaches.
- Real-time Monitoring: AI systems can monitor transactions and activities in real-time, allowing for immediate detection and response to potential threats.
- Scalability: As data volumes grow, AI-based systems can scale to meet the demand, ensuring consistent and comprehensive monitoring.
- Adaptability: AI models continuously learn from new data, improving their detection capabilities and adapting to evolving fraud tactics and anomaly patterns.
In conclusion, AI’s role in anomaly and fraud detection is pivotal in today’s digital age, where cyber threats continue to rise in sophistication and frequency.
By leveraging AI, organizations can enhance their ability to detect and respond to anomalies and fraud quickly and effectively, safeguarding their assets and maintaining the trust of their customers and stakeholders.
As AI technologies evolve, their integration into anomaly and fraud detection strategies will undoubtedly become more prevalent, offering even more significant potential to combat cyber threats and fraudulent activities.
4. AI in Network Security

Network security is a critical concern for organizations worldwide. Networks form the backbone of their IT infrastructure, facilitating data flow and communication.
Traditional network security measures often need to catch up in the face of increasingly sophisticated cyber threats.
Artificial Intelligence (AI) transforms network security by introducing capabilities that allow for more proactive, intelligent, and adaptive defense mechanisms.
Leveraging AI for Dynamic Network Protection
AI in network security involves using machine learning, deep learning, and other AI techniques to monitor, analyze, and protect network activities. By applying these technologies, AI systems can:
- Detect Anomalies: AI algorithms analyze network traffic in real-time to identify unusual patterns that may indicate a cyberattack, such as DDoS attacks, intrusion attempts, or unauthorized data exfiltration.
- Predict Threats: Advanced AI models can predict potential security threats by analyzing historical data and identifying patterns that have previously led to security incidents.
- Automate Responses: AI can automate the response to detected threats, such as isolating affected network segments or blocking malicious IP addresses, thereby reducing attackers’ window of opportunity.
Innovations in AI for Network Security Management
Several innovations highlight the progress and potential of AI in network security management:
- Adaptive Network Security Systems: These AI-driven systems can adjust security policies and defenses based on the current threat landscape. By continuously learning from new threats and adapting their configurations, these systems ensure that network defenses remain robust against evolving cyber threats.
- AI-Powered Network Segmentation: AI facilitates dynamic network segmentation, automatically adjusting network boundaries and access controls to isolate sensitive data and systems. This approach limits the potential impact of a breach by restricting lateral movement within the network.
- Behavioral Analysis for Insider Threat Detection: AI algorithms analyze user behavior to detect anomalies indicating insider threats, such as data theft or sabotage. By understanding standard user behavior patterns, AI systems can flag activities that deviate from the norm, enabling early intervention.
- Zero Trust Security Models: AI enhances Zero Trust architectures by continuously verifying the security status of devices and users within the network. This approach ensures that trust is never assumed, and access is granted based on real-time risk assessments.
The Impact of AI on Network Security
The integration of AI into network security offers several key advantages:
- Enhanced Detection Capabilities: AI’s ability to analyze vast amounts of network data in real-time enhances the detection of sophisticated cyber threats.
- Proactive Security Posture: AI enables organizations to adopt a more proactive approach to network security by predicting potential threats and automating responses.
- Reduced Operational Overhead: AI automation minimizes manual intervention, allowing security teams to focus on strategic initiatives.
- Scalability and Flexibility: AI-driven network security solutions can scale with organizational growth and adapt to changing network architectures.
In conclusion, AI is playing a transformative role in network security, providing the tools and technologies needed to protect against today’s and tomorrow’s sophisticated cyber threats. As AI technologies evolve, their integration into network security strategies will become increasingly critical, promising more secure, resilient networks that can adapt to the ever-changing cyber landscape.
5. AI in Security Automation and Response
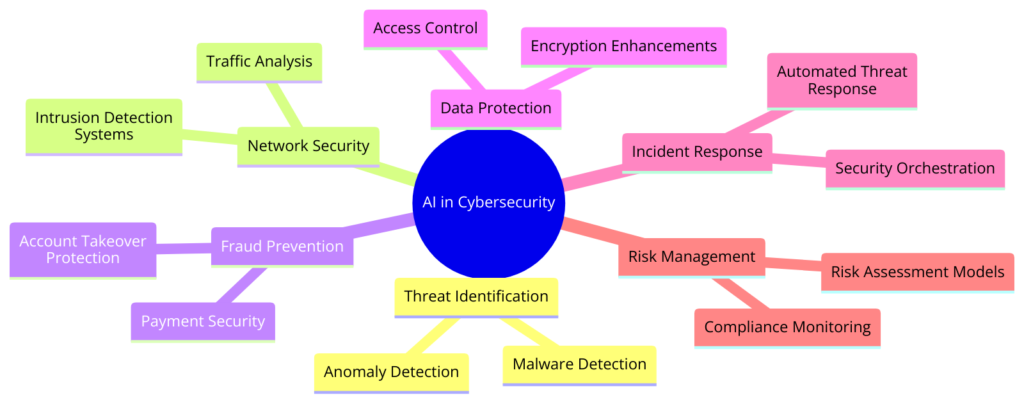
In the fast-paced world of cybersecurity, the speed and accuracy of response to threats can mean the difference between a minor incident and a major breach.
Artificial Intelligence (AI) is revolutionizing security automation and response, offering sophisticated tools that enhance an organization’s ability to swiftly and effectively address security incidents.
Automating Security Protocols with AI
AI-driven cybersecurity automation involves using machine learning algorithms and other AI technologies to automate the detection, analysis, and response to cyber threats. This automation extends across various aspects of security operations, including:
- Automated Threat Detection: AI systems continuously monitor for signs of security threats, utilizing advanced algorithms to identify malicious activity without human intervention.
- Incident Analysis and Prioritization: Upon detecting a potential threat, AI tools can analyze the severity and potential impact of the incident, automatically prioritizing it for response based on predefined criteria.
- Automated Incident Response: AI can trigger predefined response actions, such as isolating infected systems, blocking malicious IP addresses, or deploying patches, to mitigate the threat before it can cause significant damage.
Streamlining Incident Response and Resolution
The integration of AI into security operations centers (SOCs) streamlines the incident response process in several ways:
- Faster Response Times: AI’s ability to automate the detection and initial response to threats significantly reduces the time from detection to mitigation, limiting the potential impact of cyberattacks.
- Reduced Human Error: By automating routine tasks and decisions, AI reduces the risk of human error, which can be a critical factor in the successful containment and resolution of security incidents.
- Enhanced Decision Support: AI tools provide security analysts with actionable insights and recommendations, aiding decision-making during incident response efforts.
- Continuous Learning and Improvement: AI systems learn from every incident, improving their detection and response capabilities and adapting to the evolving threat landscape.
Case Studies of AI-Driven Security Automation
- Automated Malware Defense: A global financial institution implemented an AI-driven security system that automatically identifies and quarantines malware-infected devices when they attempt to connect to the network. This proactive approach has significantly reduced the incidence of malware-related breaches.
- Phishing Response Automation: An IT services company deployed an AI solution that automatically scans emails for phishing indicators, blocking suspicious emails and alerting users. The system adapts to new phishing tactics, continuously enhancing its detection accuracy.
Challenges and Considerations
While AI-driven automation and response capabilities offer numerous benefits, they also present challenges, including:
- Over-reliance on Automation: Excessive reliance on automated systems can lead to complacency, underscoring the importance of maintaining human oversight.
- Complexity of Integration: Integrating AI into existing security infrastructures can be complex, requiring significant effort to ensure compatibility and effectiveness.
- Transparency and Explainability: Ensuring that AI-driven decisions are transparent and explainable is crucial for maintaining trust and accountability in security operations.
In conclusion, AI is transforming the landscape of security automation and response, providing powerful tools that enhance the ability of organizations to respond to cybersecurity threats effectively and efficiently.
As AI technologies continue to evolve, their role in automating and streamlining security operations will undoubtedly grow, offering promising prospects for the future of cybersecurity.
6. Challenges and Ethical Considerations in AI for Cybersecurity

Integrating Artificial Intelligence (AI) into cybersecurity offers transformative potential but presents significant challenges and ethical considerations that must be carefully navigated.
As AI technologies become more pervasive in the security landscape, organizations and individuals face complex issues related to privacy, ethics, and the potential misuse of AI.
Addressing Data Privacy Concerns
One of the primary challenges in leveraging AI for cybersecurity is managing and protecting personal and sensitive data.
AI systems require access to vast amounts of data to learn, adapt, and effectively detect threats.
This raises critical questions about data privacy, including how data is collected, stored, and used and the measures in place to protect it from unauthorized access or breaches.
- Data Minimization and Anonymization: Implementing data minimization and anonymization practices can help mitigate privacy concerns by reducing the amount of personal information AI systems access and process.
- Robust Data Protection Measures: Ensuring that AI systems adhere to stringent data protection standards and regulations is crucial for safeguarding sensitive information against potential vulnerabilities.
The Potential for AI Exploitation

The sophistication of AI in cybersecurity is a double-edged sword, as cyber attackers can also exploit these technologies.
Malicious actors may utilize AI to develop more advanced cyberattacks, such as AI-powered malware that can adapt to evade detection or automated phishing attacks that are more convincing and difficult to identify.
- Adversarial AI Tactics: Cybersecurity strategies must account for attackers’ potential use of adversarial AI tactics, requiring ongoing research and development to counteract these threats effectively.
- Collaborative Security Efforts: Sharing knowledge and strategies within the cybersecurity community can help develop collective defenses against AI-powered threats.
Ethical Considerations in AI Deployment
Deploying AI in cybersecurity contexts also raises ethical considerations regarding AI systems’ decision-making processes, the transparency of AI operations, and the potential for unintended consequences.
- Transparency and Accountability: Ensuring that AI systems operate transparent and accountable is vital for maintaining trust and understanding the rationale behind AI-driven decisions.
- Bias and Fairness: AI systems must be designed and trained to avoid biases that could lead to unfair or discriminatory outcomes, particularly in decisions affecting access to information or services.
- Human Oversight: Maintaining human oversight of AI systems is essential to managing ethical concerns and allowing for human intervention in complex or sensitive situations.
Navigating the Future

Addressing these challenges and ethical considerations will be paramount as AI continues to shape the cybersecurity landscape.
Developing AI systems that are secure, ethical, and respectful of privacy requires a concerted effort from developers, policymakers, and security professionals alike.
Collaborative initiatives, rigorous ethical standards, and ongoing dialogue among stakeholders are critical for harnessing AI’s benefits in cybersecurity while mitigating its risks and moral dilemmas.
In conclusion, while AI presents a promising frontier for enhancing cybersecurity defenses, the path forward necessitates careful consideration of the associated challenges and ethical implications.
By prioritizing transparency, fairness, and privacy, the cybersecurity community can advance AI technologies that protect digital assets and uphold the values and rights of individuals and society at large.
6. The Future of AI in Cybersecurity
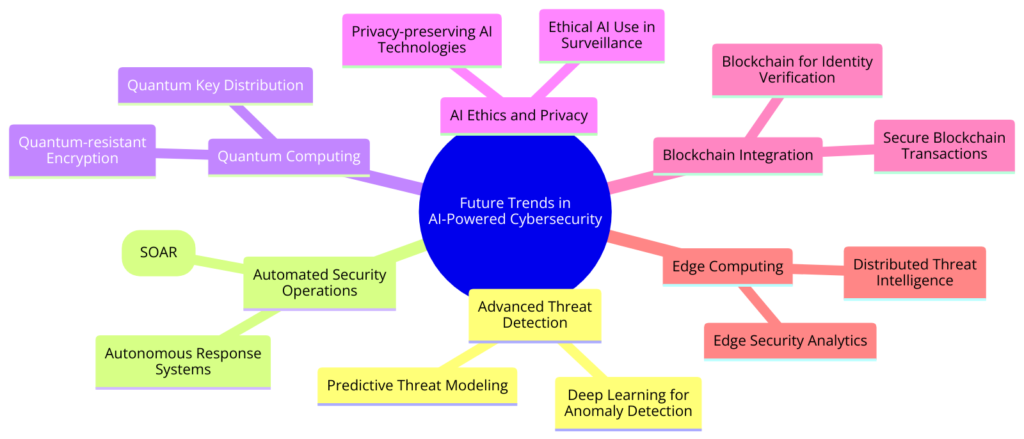
As we look toward the future, the role of Artificial Intelligence (AI) in cybersecurity is poised for significant expansion and evolution.
The rapid pace of technological advancement and the ever-changing nature of cyber threats demand a dynamic and innovative approach to digital security.
Several key trends and potential advancements will likely characterize AI’s future in cybersecurity.
Predictive Security Measures
One of the most promising aspects of AI’s future in cybersecurity is the advancement of predictive security technologies.
Leveraging AI’s capability to analyze vast datasets and identify patterns, future cybersecurity systems will detect ongoing threats and predict potential vulnerabilities and attacks before they occur.
This proactive approach could dramatically shift the cybersecurity paradigm from reactive to preventive, minimizing the impact of cyber threats.
Integration with Emerging Technologies
AI’s integration with other emerging technologies, such as blockchain and quantum computing, is expected to significantly enhance cybersecurity measures.
Blockchain could offer decentralized security solutions that are less vulnerable to single points of failure, while quantum computing has the potential to revolutionize encryption and threat modeling.
The synergy between AI and these technologies will likely result in more robust and resilient security architectures.
Autonomous Security Systems
The development of fully autonomous security systems represents another frontier for cybersecurity AI.
These systems could identify, evaluate, and respond to threats without human intervention, potentially reducing the time to respond to incidents and alleviating the workload on cybersecurity professionals.
However, realizing such systems will require careful consideration of ethical and oversight mechanisms to ensure they operate within the desired parameters.
Collaborative AI for Enhanced Threat Intelligence
The concept of collaborative AI, where multiple AI systems share insights and learn from each other, holds great promise for cybersecurity.
By pooling threat intelligence and defensive strategies, AI systems could offer a more comprehensive and unified defense against cyber threats, significantly improving the efficacy of cybersecurity measures across different organizations and sectors.
Challenges and Considerations
The journey toward these future advancements has its challenges. Issues such as ensuring the ethical use of AI, protecting against malicious actors’ misuse of AI technologies, and maintaining user privacy must be addressed.
Additionally, the increasing complexity of AI systems necessitates advanced skills and knowledge among cybersecurity professionals to manage and oversee these technologies effectively.
The future of AI in cybersecurity is exciting and uncertain. It has immense potential to transform how we protect digital assets and information.
As AI technologies evolve and integrate with other emerging technologies, the possibilities for enhancing digital security are vast.
However, realizing this potential will require ongoing innovation, collaboration, and vigilance to navigate the challenges and maximize the benefits of AI for cybersecurity.
By embracing AI’s opportunities and committing to the responsible development and deployment of AI-driven security solutions, the cybersecurity community can look forward to a future where digital threats are managed more effectively and efficiently, safeguarding our increasingly digital world against the cyber threats of tomorrow.
7. Conclusion

Exploring AI’s role in cybersecurity has illuminated its profound impact on enhancing the detection, prevention, and response to cyber threats. As we have seen, AI technologies offer unparalleled capabilities in analyzing vast datasets, identifying patterns, and automating complex decision-making processes.
This has improved the efficiency and effectiveness of cybersecurity measures and enabled a proactive stance against the constantly evolving landscape of cyber threats.
Integrating AI into various facets of cybersecurity—from threat detection and anomaly identification to network security and incident response—marks a significant shift towards more dynamic and adaptive security strategies.
These advancements have the potential to significantly reduce the time it takes to detect and mitigate cyber threats, thereby minimizing their impact and enhancing organizations’ overall security posture.
However, the journey towards fully realizing AI’s benefits in cybersecurity is challenging. Issues related to data privacy, the potential for AI exploitation by cyber attackers, and ethical considerations in AI deployment necessitate a careful and deliberate approach.
Addressing these challenges requires technological solutions, a commitment to ethical standards, and collaborative efforts within the cybersecurity community.
The future of AI in cybersecurity is promising, with the potential for predictive security measures, integration with emerging technologies, autonomous security systems, and collaborative AI offering a roadmap for innovation.
Yet, this future also demands a continued focus on the responsible development and deployment of AI technologies, ensuring that they serve to protect and enhance digital security without compromising ethical principles or user privacy.
In conclusion, AI’s transformative impact on cybersecurity practices is undeniable.
As we progress, it is imperative to encourage ongoing innovation in AI technologies while advocating for responsible use and adherence to ethical standards.
By doing so, we can harness the full potential of AI to secure our digital world against the threats of today and tomorrow.
The journey ahead is both challenging and exciting, requiring a collective effort from technologists, policymakers, and cybersecurity professionals to navigate the complexities of the digital age.
Together, we can ensure that AI continues to play a pivotal role in shaping a more secure and resilient digital future.
FAQ & Answers
1. How is AI used in cybersecurity?
AI is employed to enhance threat detection, anomaly detection, network security, and automate security protocols, offering advanced protection against cyber threats.
2. What are the challenges of using AI in cybersecurity?
Challenges include ensuring the privacy of data used in AI models, preventing the misuse of AI technologies by attackers, and keeping up with the evolving nature of cyber threats.
Quizzes
Quiz 1: “AI in Cybersecurity” – Match AI technologies to their cybersecurity applications.
Let’s match some AI technologies with their typical applications in cybersecurity. I’ll provide a list of AI technologies and their most common cybersecurity applications. For each technology, I’ll also explain how it’s used in the context of cybersecurity.
- Machine Learning (ML): Machine Learning can be used in various cybersecurity applications, including anomaly detection, malware detection, and spam detection. It helps in identifying patterns or behaviors that deviate from the norm, which could indicate a security threat.
- Deep Learning (DL): A subset of machine learning, deep learning is particularly useful in image recognition, voice recognition, and natural language processing. In cybersecurity, it can be used for phishing detection in emails and malicious activity detection in network traffic by analyzing patterns that are too complex for traditional algorithms.
- Natural Language Processing (NLP): NLP is used in cybersecurity for analyzing and understanding text-based content to detect phishing attempts, scam emails, and malicious attachments. It can also be employed in automating the analysis of cyber threat intelligence reports.
- Neural Networks: Neural networks, especially convolutional neural networks (CNNs) and recurrent neural networks (RNNs), are used in cybersecurity for anomaly detection, malware classification, and intrusion detection. Their ability to learn from sequential data makes them suitable for analyzing time-series data like network traffic.
- Generative Adversarial Networks (GANs): GANs are used in cybersecurity for generating synthetic phishing emails or websites for training purposes, improving the detection models’ accuracy. They can also be employed in testing systems’ robustness against novel attack vectors.
- Decision Trees and Random Forests: These are used for classification problems in cybersecurity, such as classifying emails as spam or not spam, or identifying whether a network activity is normal or malicious. Their interpretability helps in understanding the decision-making process, which is crucial for tweaking security measures.
- Reinforcement Learning: In cybersecurity, reinforcement learning can be used to develop adaptive systems that learn from interactions with the environment. This is particularly useful in autonomous threat response systems where the AI learns the best course of action to mitigate a threat based on past outcomes.
These technologies and their applications showcase how AI can significantly enhance cybersecurity measures by automating detection and response processes, thus reducing the time and resources required to address cyber threats.
Let’s structure the matches between AI technologies and their cybersecurity applications into a concise answer format for a quiz perspective:
- Machine Learning (ML): Anomaly Detection, Malware Detection, Spam Detection
- Deep Learning (DL): Phishing Detection, Malicious Activity Detection in Network Traffic
- Natural Language Processing (NLP): Detection of Phishing Attempts, Scam Emails, and Malicious Attachments; Automation of Cyber Threat Intelligence Analysis
- Neural Networks: Anomaly Detection, Malware Classification, Intrusion Detection
- Generative Adversarial Networks (GANs): Generating Synthetic Phishing Emails/Websites for Training, Testing Systems’ Robustness Against Novel Attack Vectors
- Decision Trees and Random Forests: Classification of Emails (Spam/Not Spam), Identification of Malicious Network Activity
- Reinforcement Learning: Development of Adaptive Threat Response Systems
These are the AI technologies matched with their corresponding applications in cybersecurity, which illustrates the diverse ways AI can be leveraged to protect against cyber threats.
Quiz 2: “Cybersecurity Innovations” – A quiz on recent AI advancements in the field of cybersecurity.
This will include hypothetical scenarios, applications, and conceptual advancements that have been significant in recent years.
Question 1: AI-Driven Threat Intelligence
What does AI-driven threat intelligence primarily aim to achieve in cybersecurity?
A) Reduce the need for human cybersecurity experts
B) Automate the process of installing security patches
C) Enhance the prediction and detection of emerging cyber threats
D) Simplify the user authentication process
Question 2: Adaptive Security Architectures
How do adaptive security architectures benefit from AI technologies?
A) They use AI to replace firewalls and antivirus software completely.
B) AI enables these systems to dynamically adjust security policies based on evolving threat landscapes.
C) They rely solely on AI for physical security measures.
D) AI simplifies regulatory compliance reporting.
Question 3: Behavioral Analytics for Insider Threat Detection
AI-based behavioral analytics can help detect insider threats by:
A) Enforcing stronger password policies
B) Monitoring and analyzing user behavior to identify anomalies that may indicate malicious activity
C) Replacing traditional authentication methods with biometrics
D) Increasing the frequency of security audits
Question 4: Deep Learning in Malware Detection
Deep learning enhances malware detection by:
A) Reducing the size of security teams needed
B) Focusing solely on virus signature updates
C) Identifying patterns and anomalies in malware code that may not be detected by traditional methods
D) Decreasing the reliance on cloud-based security solutions
Question 5: Generative Adversarial Networks (GANs) in Cybersecurity
GANs are utilized in cybersecurity to:
A) Directly attack network infrastructures as a form of stress testing
B) Generate synthetic phishing emails for training detection models
C) Replace human hackers in penetration testing teams
D) Streamline software development lifecycles
Question 6: AI in Phishing Detection and Response
AI improves phishing detection and response by:
A) Only scanning emails from unknown senders
B) Using rule-based algorithms to block spam
C) Analyzing email content in real-time to identify and quarantine phishing attempts
D) Focusing on improving email encryption
Question 7: Reinforcement Learning in Autonomous Response Systems
In the context of cybersecurity, how is reinforcement learning applied?
A) It teaches AI systems to perform routine IT maintenance tasks.
B) AI systems learn and adapt to cyber threats autonomously to devise and apply effective countermeasures.
C) It is used exclusively for social engineering attack simulations.
D) Reinforcement learning is applied to enhance the physical security of servers.
These questions cover a range of topics that demonstrate how AI technologies are applied to advance cybersecurity practices, from enhancing threat intelligence and adaptive defenses to improving malware detection and insider threat monitoring.
Here are the answers to the quiz on recent AI advancements in the field of cybersecurity:
Question 1: AI-Driven Threat Intelligence
Correct Answer: C) Enhance the prediction and detection of emerging cyber threats AI-driven threat intelligence aims to leverage machine learning and data analytics to predict and detect new and evolving cyber threats more effectively than traditional methods.
Question 2: Adaptive Security Architectures
Correct Answer: B) AI enables these systems to dynamically adjust security policies based on evolving threat landscapes. Adaptive security architectures benefit from AI by using it to analyze threats in real-time and dynamically adjust security measures and policies to address those threats effectively.
Question 3: Behavioral Analytics for Insider Threat Detection
Correct Answer: B) Monitoring and analyzing user behavior to identify anomalies that may indicate malicious activity AI-based behavioral analytics systems monitor user behavior patterns and use machine learning to identify deviations that could suggest insider threats or compromised accounts.
Question 4: Deep Learning in Malware Detection
Correct Answer: C) Identifying patterns and anomalies in malware code that may not be detected by traditional methods Deep learning can analyze vast amounts of data to identify complex patterns and anomalies in malware, improving detection rates and reducing false positives.
Question 5: Generative Adversarial Networks (GANs) in Cybersecurity
Correct Answer: B) Generate synthetic phishing emails for training detection models GANs can create realistic phishing emails or malicious URLs to train detection systems, enhancing their ability to recognize and block actual phishing attempts.
Question 6: AI in Phishing Detection and Response
Correct Answer: C) Analyzing email content in real-time to identify and quarantine phishing attempts AI enhances phishing detection and response by using natural language processing and other techniques to analyze email content and behavior, allowing for the real-time identification and quarantine of phishing emails.
Question 7: Reinforcement Learning in Autonomous Response Systems
Correct Answer: B) AI systems learn and adapt to cyber threats autonomously to devise and apply effective countermeasures. Reinforcement learning is used in cybersecurity to create systems that can autonomously learn from their environment and past actions to identify and respond to cyber threats more effectively over time.
These answers highlight how AI and machine learning technologies are being applied to enhance cybersecurity through advanced threat detection, adaptive security measures, and more efficient response strategies.